How To Fix Site Not Secure Xfinity
10 essential security tips: protect your site from hackers
You may not recall your site has anything worth being hacked for, merely websites are compromised all the time. The majority of security breaches are non to steal your data or deface your website, merely instead attempts to use your server as an email relay for spam, or to setup a temporary web server, usually to serve files of an illegal nature.
- The best antivirus software
Hacking is regularly performed by automatic scripts written to scour the Internet in an try to exploit known security issues in software. Here are our top 10 tips to assist keep you and your site safe online:
i. Keep software up to appointment
Information technology may seem obvious, just ensuring yous keep all software up to appointment is vital in keeping your site secure. This applies to both the server operating organisation and whatever software you lot may exist running on your website such as a CMS or forum. When security holes are found in software, hackers are quick to endeavor to corruption them.
If you are using a managed hosting solution then you don't need to worry and so much about applying security updates for the operating arrangement as the hosting company should have intendance of this.
If you lot are using third-party software on your website such as a CMS or forum, you should ensure you are quick to use whatever security patches. Near vendors accept a mailing list or RSS feed detailing whatever security problems. WordPress, Umbraco and many other CMSes notify y'all of available arrangement updates when y'all log in.
2. SQL injection
SQL injection attacks are when an assailant uses a spider web form field or URL parameter to gain access to or manipulate your database. When you use standard Transact SQL information technology is easy to unknowingly insert rogue lawmaking into your query that could be used to change tables, go information and delete data. You tin easily prevent this by ever using parameterised queries, nigh web languages take this feature and information technology is easy to implement.
Consider this query:
"SELECT * FROM tabular array WHERE column = '" + parameter + "';" If an aggressor inverse the URL parameter to pass in ' or 'ane'='1 this will cause the query to look similar this:
"SELECT * FROM table WHERE column = '' OR 'i'='ane';" Since '1' is equal to 'one' this will allow the attacker to add an additional query to the end of the SQL statement which will as well exist executed.
3. XSS
Cross site scripting is when an assailant tries to laissez passer in JavaScript or other scripting code into a spider web form to attempt to run malicious code for visitors of your site. When creating a form e'er ensure y'all bank check the data being submitted and encode or strip out any HTML.
4. Error messages
Be conscientious with how much data you give abroad in your error messages. For case if you have a login course on your website you should retrieve about the language you use to communicate failure when attempting logins. Yous should use generic messages like "Incorrect username or countersign" every bit not to specify when a user got half of the query right. If an aggressor tries a beast force attack to go a username and countersign and the error bulletin gives abroad when one of the fields are right and then the attacker knows he has ane of the fields and can concentrate on the other field.
five. Server side validation/form validation
Validation should always be done both on the browser and server side. The browser tin can catch simple failures similar mandatory fields that are empty and when y'all enter text into a numbers only field. These can however exist bypassed, and you should brand sure you cheque for these validation and deeper validation server side as declining to practice and then could lead to malicious code or scripting code being inserted into the database or could cause undesirable results in your website.
6. Passwords
Everyone knows they should utilise complex passwords, just that doesn't mean they always do. It is crucial to utilize stiff passwords to your server and website admin area, only as as well important to insist on good countersign practices for your users to protect the security of their accounts.
Equally much equally users may not like it, enforcing password requirements such equally a minimum of around eight characters, including an capital letter and number will assist to protect their information in the long run.
Passwords should ever be stored as encrypted values, preferably using a i style hashing algorithm such as SHA. Using this method means when you are authenticating users you are only ever comparing encrypted values. For extra security it is a good idea to salt the passwords, using a new common salt per password.
In the event of someone hacking in and stealing your passwords, using hashed passwords could assist damage limitation, every bit decrypting them is not possible. The all-time someone tin practice is a dictionary assail or brute strength attack, essentially guessing every combination until it finds a match. When using salted passwords the process of cracking a big number of passwords is even slower as every guess has to be hashed separately for every table salt + password which is computationally very expensive.
Thankfully, many CMSes provide user management out of the box with a lot of these security features built in, although some configuration or actress modules might be required to apply salted passwords (pre Drupal seven) or to set the minimum password strength. If y'all are using .NET and then information technology'due south worth using membership providers as they are very configurable, provide inbuilt security and include readymade controls for login and countersign reset.
7. File uploads
Assuasive users to upload files to your website can be a large security risk, even if it's simply to alter their avatar. The hazard is that whatsoever file uploaded even so innocent it may wait, could contain a script that when executed on your server completely opens up your website.
If you have a file upload form then you need to treat all files with great suspicion. If yous are allowing users to upload images, you cannot rely on the file extension or the mime blazon to verify that the file is an prototype as these can easily exist faked. Fifty-fifty opening the file and reading the header, or using functions to check the image size are non total proof. Most images formats allow storing a annotate section which could contain PHP code that could be executed by the server.
Then what can you do to prevent this? Ultimately you want to terminate users from existence able to execute any file they upload. Past default web servers won't attempt to execute files with paradigm extensions, but it isn't recommended to rely solely on checking the file extension as a file with the proper name image.jpg.php has been known to go through.
Some options are to rename the file on upload to ensure the correct file extension, or to change the file permissions, for example, chmod 0666 so it can't be executed. If using *nix y'all could create a .htaccess file (see below) that will only let access to gear up files preventing the double extension attack mentioned before.
deny from all<Files "^\w+\.(gif|jpe?k|png)$">order deny,allowallow from all</Files> Ultimately, the recommended solution is to prevent direct access to uploaded files all together. This way, any files uploaded to your website are stored in a folder outside of the webroot or in the database as a hulk. If your files are non directly accessible you volition need to create a script to fetch the files from the private folder (or an HTTP handler in .Cyberspace) and evangelize them to the browser. Epitome tags back up an src attribute that is not a direct URL to an image, so your src attribute tin can indicate to your file commitment script providing yous set the correct content type in the HTTP header. For example:
<img src="/imageDelivery.php?id=1234" /><?php // imageDelivery.php // Fetch image filename from database based on $_GET["id"] ... // Evangelize epitome to browser Header('Content-Type: image/gif'); readfile('images/'.$fileName); ?> eight. Server security
Most hosting providers deal with the server configuration for yous, just if you are hosting your website on your own server then there are few things you will want to check.
Ensure you accept a firewall setup, and are blocking all not essential ports. If possible setting up a DMZ (Demilitarised Zone) merely allowing admission to port 80 and 443 from the outside world. Although this might not be possible if you don't have access to your server from an internal network equally y'all would need to open up ports to allow uploading files and to remotely log in to your server over SSH or RDP.
If you are allowing files to be uploaded from the Net simply use secure transport methods to your server such as SFTP or SSH.
If possible have your database running on a different server to that of your web server. Doing this means the database server cannot be accessed directly from the outside globe, only your web server can access it, minimising the risk of your data being exposed.
Finally, don't forget about restricting concrete admission to your server.
9.SSL
SSL is a protocol used to provide security over the Internet. Information technology is a good idea to employ a security document whenever y'all are passing personal data betwixt the website and web server or database. Attackers could sniff for this information and if the communication medium is not secure could capture it and utilize this information to proceeds access to user accounts and personal information.
Once yous think you take washed all you can to secure your website and then it's time to test your security. The near effective fashion of doing this is via the use of some security tools, often referred to as penetration testing or pen testing for brusque.
At that place are many commercial and free products to assist you with this. They work on a like footing to scripts hackers will use in that they test all know exploits and attempt to compromise your site using some of the previous mentioned methods such equally SQL injection.
Some free tools that are worth looking at:
- Netsparker (Free community edition and trial version bachelor). Expert for testing SQL injection and XSS
- OpenVAS. Claims to be the almost advanced open source security scanner. Good for testing known vulnerabilities, currently scans over 25,000. But it can be difficult to setup and requires a OpenVAS server to be installed which only runs on *nothing. OpenVAS is fork of a Nessus (opens in new tab)earlier it became a closed-source commercial product.
The results from automated tests can be daunting, equally they present a wealth of potential issues. The important thing is to focus on the critical issues first. Each issue reported normally comes with a proficient explanation of the potential vulnerability. You lot volition probably detect that some of the medium/low problems aren't a concern for your site.
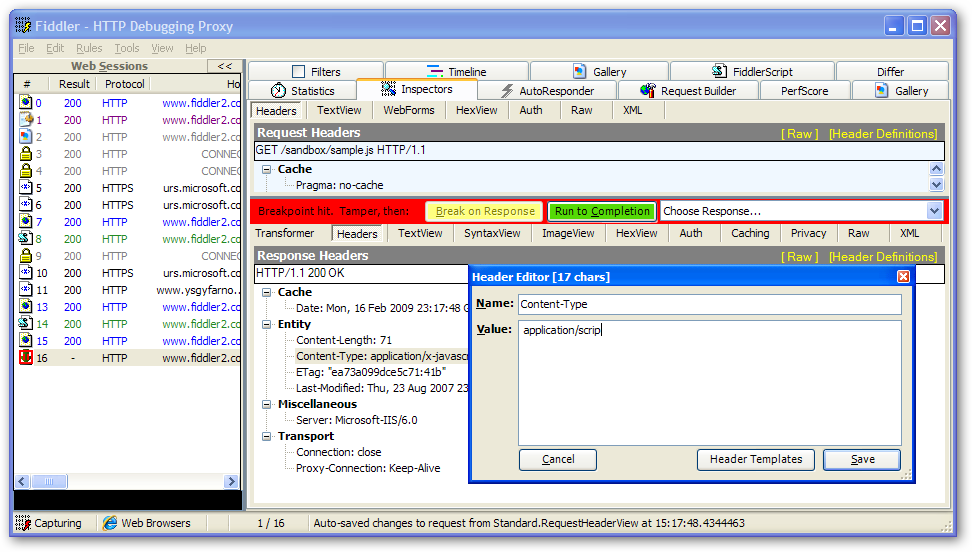
If you wish to take things a step further so there are some further steps you tin accept to manually try to compromise your site by altering Postal service/Go values. A debugging proxy tin assist you here as it allows you to intercept the values of an HTTP asking betwixt your browser and the server. A pop freeware application chosen Fiddler is a good starting bespeak.
So what should you be trying to alter on the request? If you accept pages which should only be visible to a logged in user then I would try changing URL parameters such as user id, or cookie values in an attempt to view details of some other user. Another area worth testing are forms, changing the Mail values to try to submit lawmaking to perform XSS or to upload a server side script.
Hopefully these tips will assist keep your site and information safety. Thankfully virtually CMSes have a lot of inbuilt security features, simply it is a still a good idea to have knowledge of the virtually common security exploits and so you lot can ensure you are covered.
There are also some helpful modules available for CMSes to check your installation for mutual security flaws such equally Security Review for Drupal and WP Security Browse for WordPress.

Thank you for reading 5 articles this month* Bring together at present for unlimited admission
Savor your first month for only £1 / $i / €1
*Read 5 gratuitous articles per month without a subscription

Join now for unlimited access
Try outset month for just £i / $1 / €one
Related articles
How To Fix Site Not Secure Xfinity,
Source: https://www.creativebloq.com/netmag/10-essential-security-tips-protect-your-site-hackers-7126222
Posted by: hunttherlhe.blogspot.com


0 Response to "How To Fix Site Not Secure Xfinity"
Post a Comment